Cybersecurity Trends for 2025: Safeguarding Non-Enterprise Businesses

It sounds like it is the opening of a Science Fiction novel… “In the year 2025, Cybersecurity threats are more advanced, evasive, and damaging than ever…” But the reality is that it is not from Sci-Fi, but real life, and the Cybersecurity threats pose a real danger, especially for non-enterprise businesses earning between $1 million and $100 million in annual revenue. These companies, often operating with lean IT and security teams, face a rapidly evolving digital threat landscape that demands increased vigilance and proactive investment.
The Evolving Threat Landscape
In the year 2025, businesses are facing an unprecedented number and level of evolving Cybersecurity threats attacking their businesses. One of the most dangerous new developments is the rise of Highly Evasive Adaptive Threats (HEATs). These attacks leverage dynamic web content, obfuscated JavaScript, and ephemeral URLs to bypass traditional defenses such as email filters, antivirus software, and web gateways. HEATs target common workflows such as browsers, email platforms, and collaboration tools, which makes them particularly effective against the unsuspecting teams of Small to Medium sized Businesses (SMBs).
New Cyber Threats in the year 2025
Another significant threat is the surge of AI-powered social engineering and deepfake technology. Cybercriminals are now using generative AI to craft hyper-personalized phishing emails, clone executive voices, and produce realistic video scams at scale. According to research, AI-enhanced phishing attacks are nearly twice as successful as those created manually. For Small to Medium sized Businesses (SMBs), even a single successful impersonation call could have devastating financial or reputational consequences.
Compounding the threat, most new cyberattacks are now malware-free, relying instead on credential theft, misconfigurations, and remote exploitation. The increasing use of cloud services and third-party providers further expands the attack surface, making supply chain compromises a growing concern. In addition, geopolitical tensions and state-sponsored cyber operations are spilling into the private sector, affecting even non-enterprise firms with DDoS attacks and data theft.
Prompt injection attacks, where adversaries embed malicious commands into seemingly benign inputs for AI systems, are another emerging threat in 2025. With more businesses integrating generative AI tools into their workflows - from document generation to customer service - these vulnerabilities pose serious risks. When compromised, internal AI systems can leak sensitive data and/or generate harmful outputs and content.
Why Cybersecurity is More Critical Than Ever
The imperative for enhanced cybersecurity has never been greater. Small and mid-sized businesses are now just as likely to be targeted as large enterprises, especially due to the scalable nature of today’s attacks. Automated adversaries can identify vulnerabilities in minutes, rendering traditional perimeter defenses obsolete. At the same time, these businesses often operate hybrid environments that combine cloud, on-premise, and mobile infrastructures, introducing security complexity without the corresponding security resources. According to CompTIA , many organizations cite staffing and budget as the biggest barriers to cybersecurity maturity, making it essential to adopt modern, scalable defense strategies.
Emerging Security Trends and Best Practices
To combat these threats, several new trends are shaping cybersecurity practices in 2025. AI-augmented defense platforms, such as extended detection and response (XDR) systems, are being adopted to analyze behaviors across networks, endpoints, and cloud environments. These platforms use machine learning and signal intelligence to detect and respond to advanced persistent threats. Autonomous threat-hunting tools have also matured, enabling proactive discovery of hidden attackers without requiring human analysts to manually comb through logs. Tools like CyberSentinel and frameworks such as "Asymmetry by Design " offer AI-driven anomaly detection and rapid response capabilities.
Zero Trust security models continue to gain traction, particularly among non-enterprise businesses. These models operate on the principle that no user, device, or system is inherently trustworthy. As such, organizations are increasingly deploying multifactor authentication (MFA), implementing least-privilege access controls, and using continuous identity verification. Deception technologies (like honeypots and moving-target defenses) are also being used more widely to mislead and trap attackers while alerting defenders to potential breaches.
For more on different security models, check out our blog on Building Resilience and Recovery Protocols into Your Security Strategy .
Planning for Quantum and Cyber-Physical Convergence
Forward-thinking businesses are beginning to prepare for quantum computing risks by evaluating and implementing post-quantum cryptography (PQC). Though still in its early stages, PQC is critical for protecting long-term data against future quantum threats. Companies are starting to inventory their cryptographic assets and exploring hybrid encryption methods to stay ahead.
Meanwhile, the convergence of cyber and physical security is becoming a key concern, especially for firms using IoT and operational technologies. Unified governance is required to ensure these systems are not exploited through overlapping vulnerabilities. On the human side, employee readiness is being prioritized through adaptive training and phishing simulations, replacing outdated annual compliance courses with interactive, scenario-based learning.
AI as a Tool for Both Attack and Defense

Artificial intelligence is a double-edged sword in this new era. On the offensive side, attackers are deploying AI to create more convincing phishing campaigns, automate vulnerability scanning, and generate malicious deepfakes. They are even developing autonomous AI agents capable of probing defenses and launching attacks without human oversight. Prompt injection attacks against corporate AI systems further demonstrate how generative AI can be exploited.
Conversely, AI is also powering defensive innovations. Modern Security Operations Centers (SOCs) now rely on AI to triage alerts, reduce noise, and speed up incident response. AI systems can analyze terabytes of telemetry data in real time to detect anomalies that human analysts might miss. Agentic response systems, driven by AI, can orchestrate containment and remediation automatically. Additionally, proactive AI tools are being used for internal red teaming and pentesting, identifying vulnerabilities before adversaries can.
Website and Web Application Security
Developers should implement secure coding standards and regularly scan code using automated tools such as SonarQube , Snyk , or Veracode to identify vulnerabilities. Following the OWASP Top 10 guidelines helps prevent common web threats like SQL injection, cross-site scripting (XSS), and insecure authentication. Agencies should also ensure secure deployment configurations and enable HTTPS by default. Web application firewalls (WAFs) like Cloudflare or AWS WAF provide an additional layer of runtime protection.
Securing Internal AI Tools
For AI systems, especially those processing sensitive data, security starts with input validation to guard against prompt injection attacks. Developers should implement access controls, API security, and audit logs. Using tools like Azure AI Content Safety , Google’s Vertex AI Guardrails , or open-source solutions like Guardrails AI can help monitor and manage safe model responses. AI models should be trained and hosted in secure environments with encryption applied both at rest and in transit.
Mobile Application Security
Mobile apps must be designed with privacy and security from day one. Development teams should enforce strong authentication (e.g., biometrics, MFA), secure local data storage using encrypted containers, and protect API endpoints with tokens and rate limiting. Tools like Mobile App Security Testing (MAST) platforms such as; NowSecure , Zimperium , and AppSweep , can uncover vulnerabilities early. Regular penetration testing and code reviews should also be integrated into the release process.
Adopting DevSecOps and Security Training
All teams involved in software development should be trained in secure coding practices and DevSecOps principles. Embedding security tools like GitHub Advanced Security , Checkmarx , or GitLab Secure into CI/CD pipelines ensures vulnerabilities are caught early. Shift-left security (testing during development rather than after deployment) improves both speed and safety. Agencies should be required to follow formal secure development lifecycle (SDLC) models and document their security compliance practices.
By proactively embedding cybersecurity into development processes and using the right tools and frameworks, businesses can drastically reduce their risk exposure and ensure that new digital products do not become new vulnerabilities.
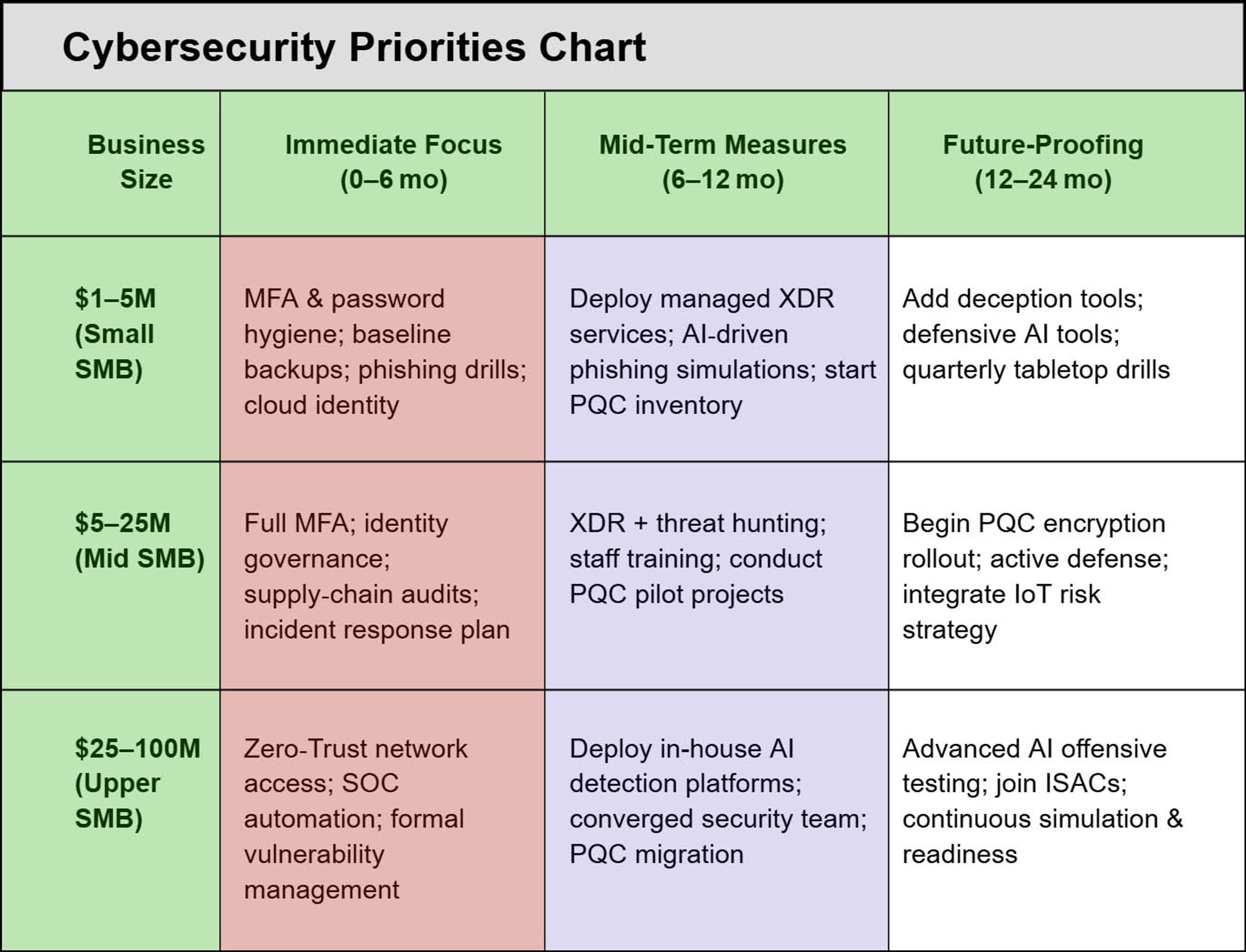
Strategic Priorities by Business Size
To navigate the cybersecurity demands of 2025, non-enterprise businesses must tailor their strategies based on their size and their operational complexity. Smaller firms with $1–5 million in revenue should begin with the basics: enforcing MFA, educating employees on phishing, and securing cloud identities. As they mature, deploying managed XDR services and deception tools can significantly improve security without requiring in-house teams. Mid-sized firms ($5–25 million) should prioritize full Zero Trust adoption, establish incident response plans, and start piloting post-quantum cryptography projects. Businesses on the higher end of the spectrum ($25–100 million) need to invest in SOC automation, in-house AI defense platforms, and cyber-physical convergence strategies.
Conclusion: A Tailored Approach to Resilience

Ultimately, cybersecurity in 2025 is not about doing everything -it's about doing the right things first. By understanding the newest threats, adopting the latest defensive tools, and aligning cybersecurity strategies to their size and complexity, non-enterprise businesses can build resilience in a rapidly evolving digital world.
In addition to doing the right things first, it is critical that businesses practice a consistent Cybersecurity strategy by annually evaluating their situation and Cybersecurity efforts. Cyber Threats are always changing and evolving and it takes a consistent effort to stay up to date and make sure that you are still doing the right things first to maintain your businesses Cybersecurity.
ScreamingBox uses the latest Cybersecurity tools and best practices in all the software we develop for our clients. Please CONTACT US if you wish to discuss how we can help secure your businesses software product development.
For more information on Cybersecurity Strategies, please check out our Podcast with Steve Orrin, Federal CTO & Sr. Principal Engineer of Intel .
ScreamingBox's digital product experts are ready to help you grow. What are you building now?
ScreamingBox provides quick turn-around and turnkey digital product development by leveraging the power of remote developers, designers, and strategists. We are able to deliver the scalability and flexibility of a digital agency while maintaining the competitive cost, friendliness and accountability of a freelancer. Efficient Pricing, High Quality and Senior Level Experience is the ScreamingBox result. Let's discuss how we can help with your development needs, please fill out the form below and we will contact you to set-up a call.